Earlier today, I posted an article to show you how to Install MacOS Sierra 10.12 on VirtualBox on Windows. Some of the process is similar, but I’ll walk you through
Tag: Microsoft

Last month, Apple released their final version of MacOS Sierra. If you have decent hardware with enough CPU, RAM, and storage space, you could create a MacOS Sierra virtual machine
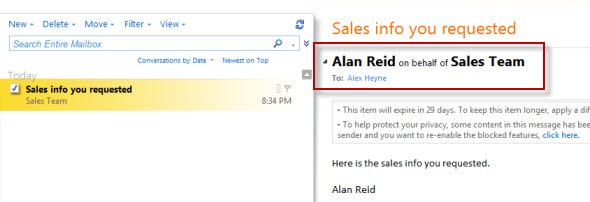
If you’re a Microsoft Exchange administrator, you might have come across a request from a user wanting to either Send On Behalf of a Distribution Group they’re a member of,
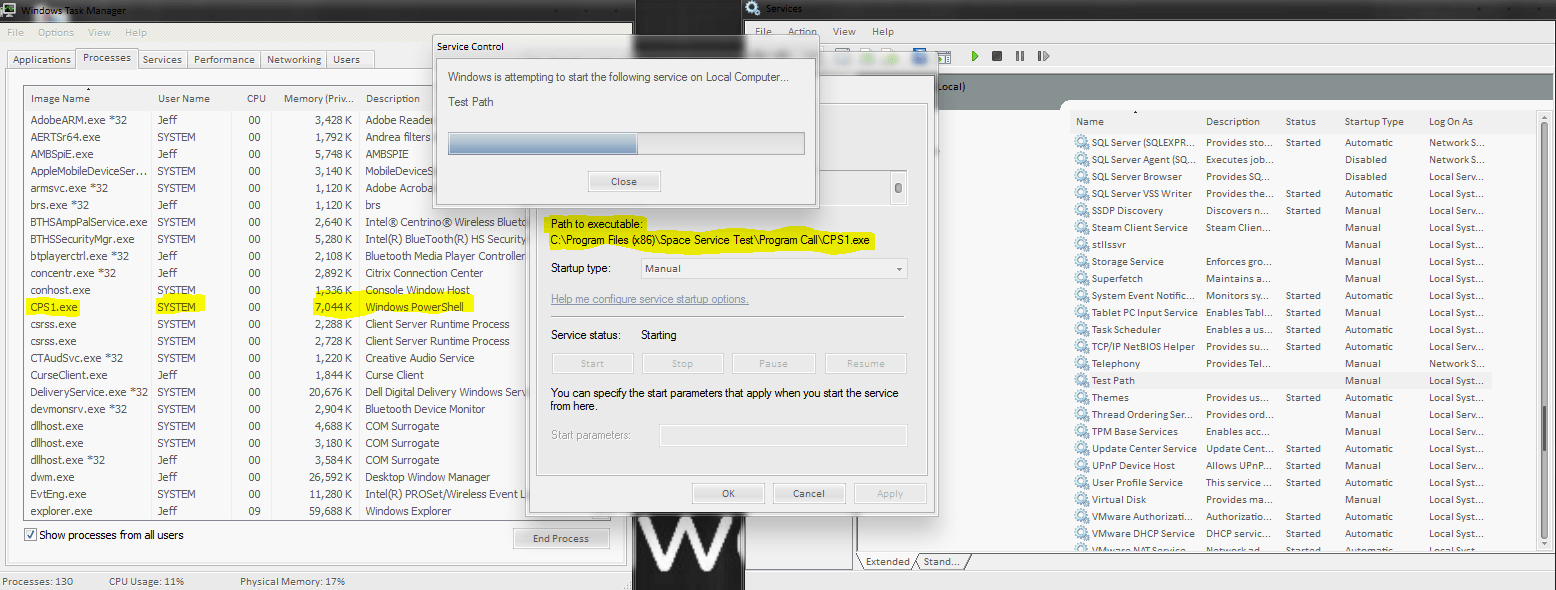
If you’re using a vulnerability scanner on your PC or network, you’ve probably come across the Microsoft Windows Unquoted Service Path Enumeration vulnerability. The truth is, this vulnerability has been

If you have a local computer that is not on a domain, since Windows XP, you cannot access the admin shares or have WMI access using a local account, even
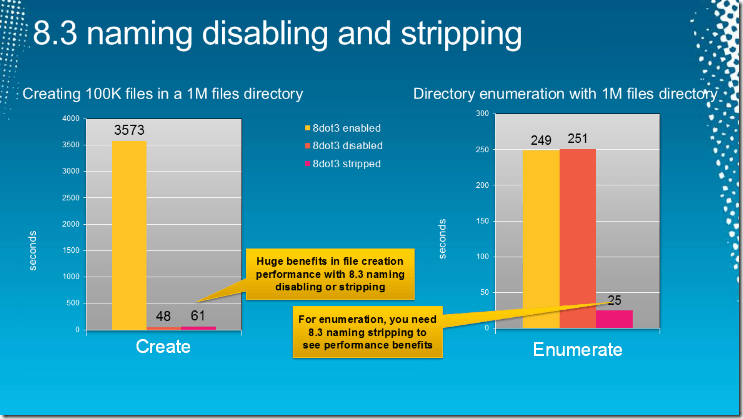
There are performance and security benefits to disabling short file names (or 8.3 file names) on a Windows Server. From the graph below, you can see the performance benefits of

I was recently working on an older computer that needed a fresh installation of Windows 7. I downloaded a fresh image of Windows 7 with SP1 and ran through the

If you run any Windows Servers, you may run into a scenario where you want to remove access to Internet Explorer. Usually, any administrators that log into servers won’t have

There are a few options you have if you want to enable audit logging on Microsoft SQL Server. You can write the logs to a .sqlaudit file, but you cannot


