MacOS Tahoe is right around the corner and with the first beta and WWDC announcement, Apple is changing the Launchpad, actually completely replacing it. Instead of the Launchpad in your

If you’re a Mac user, or manage file shares where Macs are present, you’ve probably seen the .DS_Store file in your file share folders or removable media. The .DS_Store (Desktop

WP-Cron is a core component of WordPress since it is used for many scheduled tasks including WordPress updates, plugin updates, and other core and plugin functionality. Server configuration, access controls,

There are times when your Contacts app on your Mac might get out of sync with iCloud. In my case, the Contacts app kept showing contacts and data from over
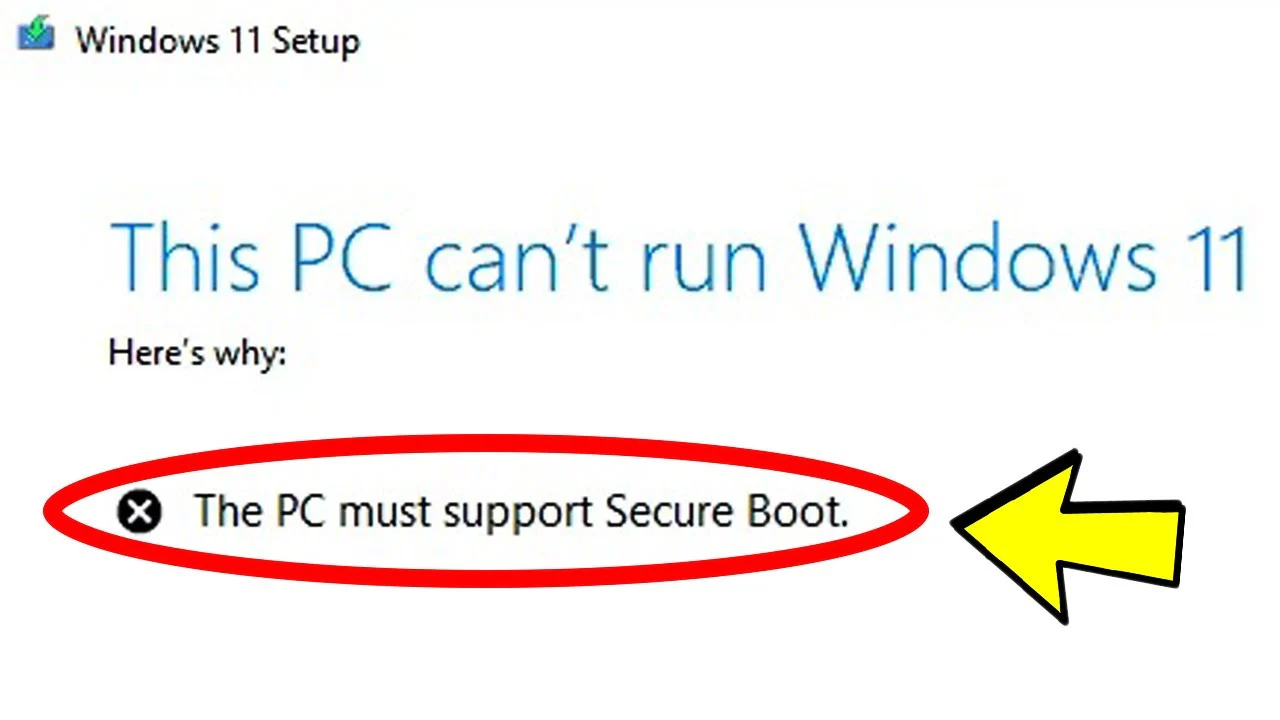
Secure Boot is a core technology in your systems BIOS that ensures only trusted operating systems can boot on the device. Secure Boot is enabled by default on most PCs,

I just got my hands on the Lenovo Legion Y700 2023 Android tablet. I ordered the Chinese model with the original Chinese CN ROM because I wanted the higher specs

Everywhere you turn, data is be collected about you and your internet activity, usually referred to as telemetry. Luckily, there are steps you can take to help minimize the amount
Windows 11 can suffer from slow performance issues just like previous versions of Windows. There are a few things you can do as a user to help speed up Windows
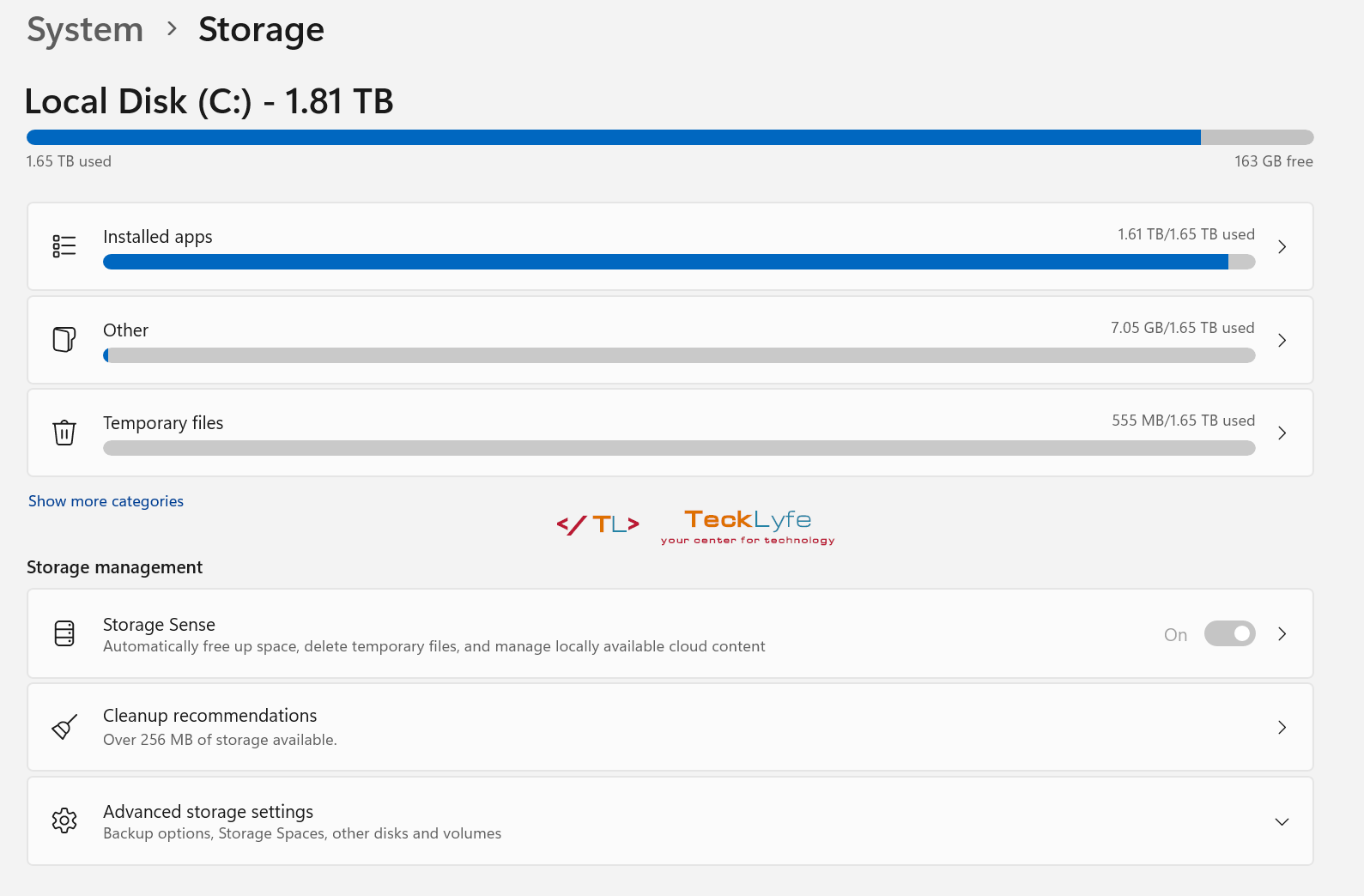
Keeping your Windows 11 disk clean can help speed up performance and keep everything running smooth. There are a few options to cleanup old and temporary files and Windows 11
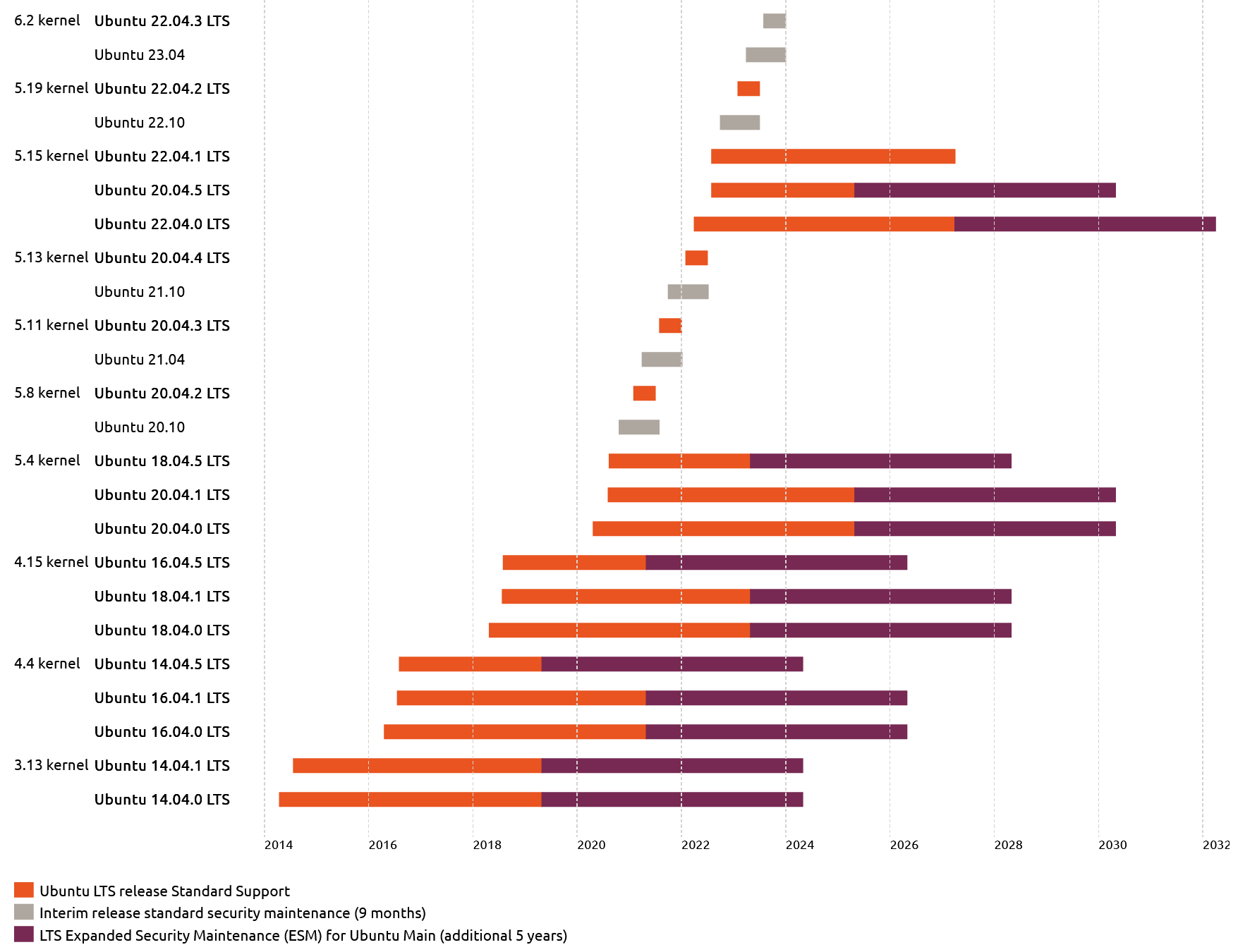
Linux Kernel 6.2 was made available to Ubuntu 22.04 LTS a few months ago. Usually, you can get updated to the latest version using the normal apt commands like apt

