If you’re using a vulnerability scanner on your PC or network, you’ve probably come across the Microsoft Windows Unquoted Service Path Enumeration vulnerability. The truth is, this vulnerability has been around for many years and Microsoft hasn’t done much to address it. Instead, they’ve left it up to the individual developers to fix their programs and include quotes around their service paths when creating the registry keys.
The Microsoft Windows Unquoted Service Path Enumeration Vulnerability
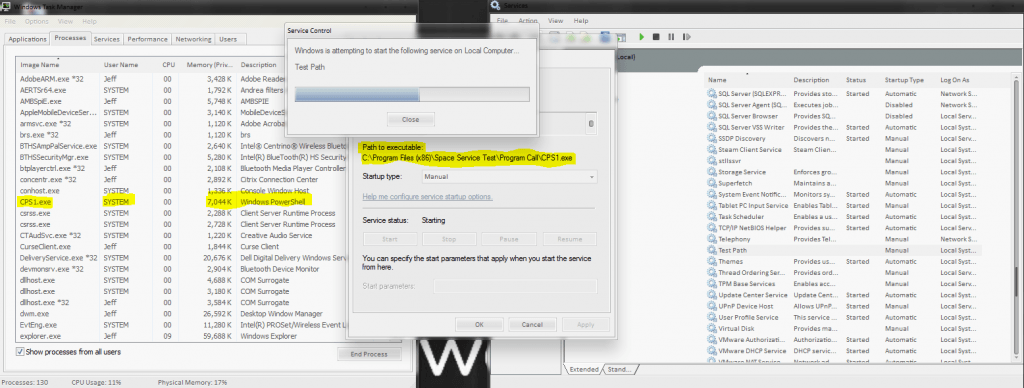
All Windows services have a Path to its executable. If that path is unquoted and contains whitespace or other separators, then the service will attempt to access a resource in the parent path first. This affects all versions of Windows and any Operating System that supports spaces in file names.
Essentially, if you have an unquoted service path with a space in it, that service is vulnerable to attack. If an attacker has access to a folder in the directory path, it is possible for privilege escalation to take place by inserting a malicious program in the parent path before the whitespace.
Disclaimer: Remember to check your results! I cannot be liable for any damage caused by running these scripts. It’s your environment and you ran them.
I’ve seen a few scripts floating around to resolve this vulnerability. Some can be run on individual systems and others are Powershell scripts that can be run across a network. I would recommend starting small and thoroughly test your results.
Remediation for Microsoft Windows Unquoted Service Path Enumeration Vulnerability
The first step you can do on a PC is run this command from an elevated command prompt. This will scan your registry and display all of the service paths that need remediation.
wmic service get name,displayname,pathname,startmode |findstr /i "auto" |findstr /i /v "c:windows\" |findstr /i /v """
Alternate Powershell version:
cmd /c 'wmic service get name,displayname,pathname,startmode |findstr /i "auto" |findstr /i /v "c:windows\" |findstr /i /v """'
There’s a nifty Powershelly script over at VectorBCO’s GitHub Project.
Before running the Powershell script, you might need to set your ExecutionPolicy to Unrestricted if you haven’t already. To do that, run this command in Powershell and select Y:
Set-ExecutionPolicy Unrestricted
Conclusion
Depending on how you manage your servers, you should have a few options to deploy this Powershell script to multiple systems. Not every server will have this vulnerability unless the same affected software is installed on every server.