Log4j is a Java library for logging error messages in applications and is a critical security vulnerability with a severity score of 10 out of 10. The high score is
Category: Security

According to Microsoft Security Advisory ADV190023, a future Windows Update in 2020 will make changes to LDAP Signing (LDAPS) and will require connections to use LDAPS instead of the less-secure

Docker is a great alternative to virtualization, especially in the case of Linux if you don’t need a GUI. Most of the popular Kali Linux pentest tools are command-line based

Everything seems to be moving to “the cloud” these days, and you have a few options such as Microsoft Azure and Amazon AWS to name a few. Depending on your

If you followed my previous guides for LEMP Install NGINX PHP7 MySQL on Ubuntu 16.04 Server then you probably installed NGINX from the Ubuntu repo. Unfortunately, the version in the

Fix SQL Cluster Encryption Error TDSSNIClient initialization failed with error 0xd, status code 0x38
For general instructions on how to Force Encryption on a SQL Server Instance, follow Microsoft KB Artcile How to enable SSL encryption for an instance of SQL Server by using
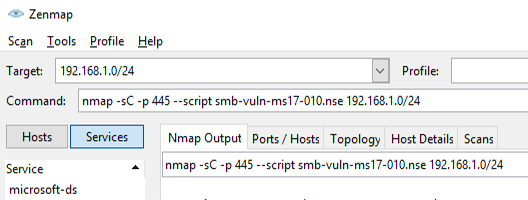
With the recent spread of the #WannaCry (Update 6/27/17: and #Petya) ransomware over the past week, the IT community has been in a frenzy to patch vulnerable systems that are
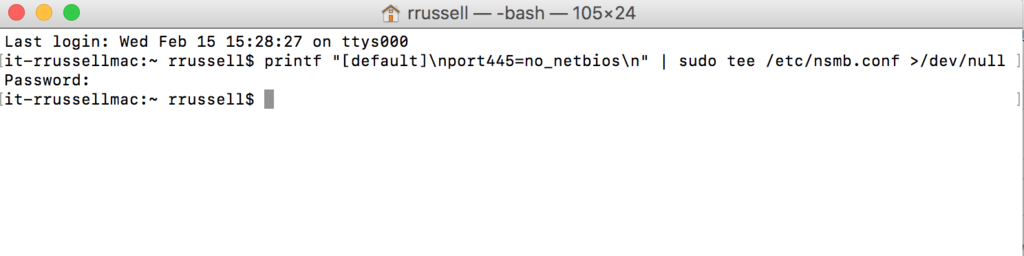
Even though my network has NetBIOS disabled in my Windows environment, including on the Windows DHCP server, the Mac OS X computers on the network still want to send NetBIOS

MongoDB is “a document database that provides high performance, high availability, and easy scalability”. In this chapter of our InfoSec System Hardening series, we’ll walk you through some of the

The next segment in our InfoSec System Hardening series is how to harden an NGINX Web Server. NGINX is an alternative to the popular Apache Web Server on Linux. In

