In Windows, the taskbar thumbnail preview allows you to hover your mouse over the application icon and see previews of multiple windows you have open, similar to the screenshot above.

Earlier today, I posted an article to show you how to Install MacOS Sierra 10.12 on VirtualBox on Windows. Some of the process is similar, but I’ll walk you through

Last month, Apple released their final version of MacOS Sierra. If you have decent hardware with enough CPU, RAM, and storage space, you could create a MacOS Sierra virtual machine
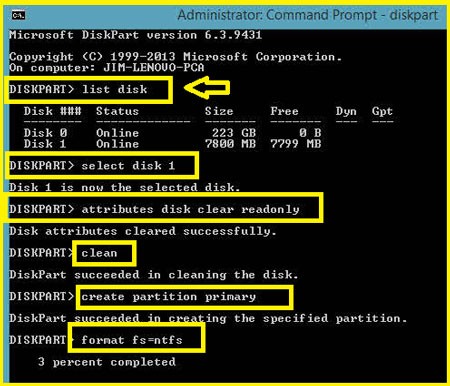
There are times when Windows doesn’t want to format a USB drive. You might get an error saying the drive is write-protected, or you’ll get an error saying it just
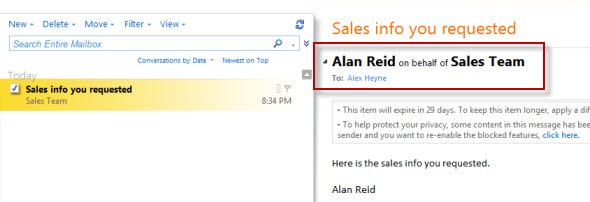
If you’re a Microsoft Exchange administrator, you might have come across a request from a user wanting to either Send On Behalf of a Distribution Group they’re a member of,
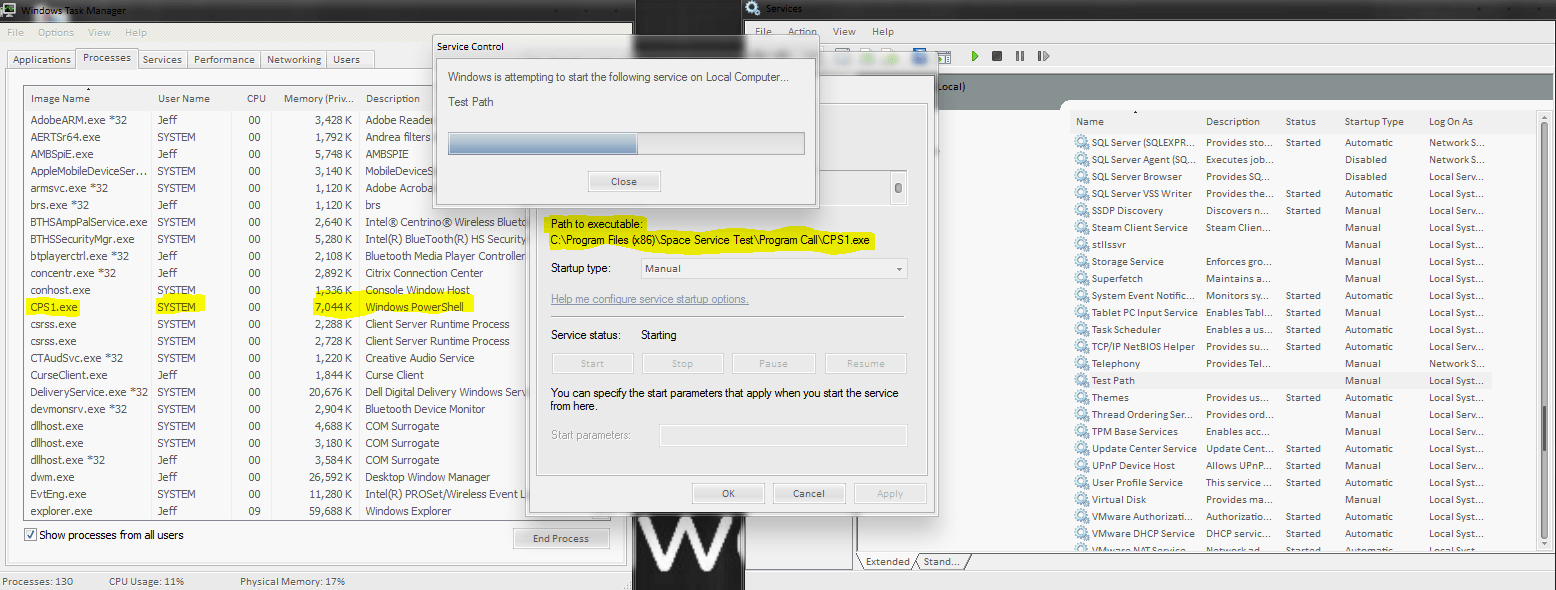
If you’re using a vulnerability scanner on your PC or network, you’ve probably come across the Microsoft Windows Unquoted Service Path Enumeration vulnerability. The truth is, this vulnerability has been

If you’re a blogger or a web developer, there will hopefully come a time when you out-grow a shared host and need either a VPS or a dedicated server to

As many of us begin to upgrade to iOS 10 that was launched earlier today, we recommend that you check some of these settings to ensure your security and privacy

Tor is free software and an open network. Tor protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents