With the recent spread of the #WannaCry (Update 6/27/17: and #Petya) ransomware over the past week, the IT community has been in a frenzy to patch vulnerable systems that are missing the MS17-010 patch that Microsoft released back in March 2017. If you need to scan your network for possible vulnerable systems, you can use a tool called NMap (or ZenMap for a GUI interface in Windows), with this NSE script available on GitHub. According to the GitHub description, “Attempts to detect if a Microsoft SMBv1 server is vulnerable to a remote code execution vulnerability (ms2017-010). The script connects to the $IPC tree, executes a transaction on FID 0 and checks if the error “STATUS_INSUFF_SERVER_RESOURCES” is returned to determine if the target is not patched against CVE2017-010. Tested on a vulnerable Windows 7. We might have some issues with v2 protocols with signing enabled.”
Downloading The NSE smb-vuln-ms17-010.nse Script
Update: Update to version NMap 7.50 to get the most recent NSE script available.
Download smb-vuln-ms17-010.nse from GitHub
Save it to Nmap NSE script directory:
- Linux – /usr/share/nmap/scripts/ or /usr/local/share/nmap/scripts/
- OSX – /opt/local/share/nmap/scripts/
- Windows ZenMap Install – C:\Program Files (x86)\Nmap\scripts
Using the NSE smb-vuln-ms17-010.nse Script
If you’re using the command line version of NMap on any system, you can run this command (change the IP range to meet your needs):
nmap -sC -p 445 --script smb-vuln-ms17-010.nse 192.168.1.0/24
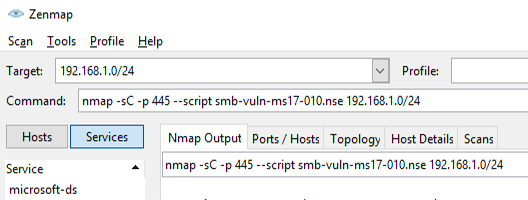
If you’re using the Windows ZenMap GUI, fill in the Target box with your IP (or IP range) and use this line in the Command box (it should automatically append the IP/Range to the end of this command):
nmap -sC -p 445 --script smb-vuln-ms17-010.nse
Scan Results
If the scan finds a possibly vulnerable server, you’ll get a result like this:
Starting Nmap 7.40 ( https://nmap.org ) at 2017-05-17 13:18 Central Daylight Time
Nmap scan report for 192.168.1.50
Host is up (0.014s latency).
PORT STATE SERVICE
445/tcp open microsoft-dsHost script results:
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
|_ https://technet.microsoft.com/en-us/library/security/ms17-010.aspxNmap done: 1 IP address (1 host up) scanned in 0.98 seconds
What To Do Next
If you find a vulnerable machine, you’ll want to patch it right away. You can use the following references to find information for your Operating System version:
As a general rule, don’t rely on this NMap script to find all of your vulnerable systems, this is only a tool. Stay current on patching workstations and servers.