As with any server, whether it be a web server, file server, database server, etc, hardening is an important step in information security and protecting the data on your systems.
Category: Security

A zero-day local privilege escalation vulnerability has been found in the Linux kernel that has existed since 2005, being called DirtyCow. This bug affects a large number of popular Linux

If you’re running a WordPress site on a Linux server running NGINX, then you might be interested in setting up a free SSL (HTTPS) certificate using Let’s Encrypt. The internet
As of yesterday, all of Facebook’s 900 million Messenger users should be able to choose to have specific chat threads use end-to-end encryption, protecting a message from all eyes except
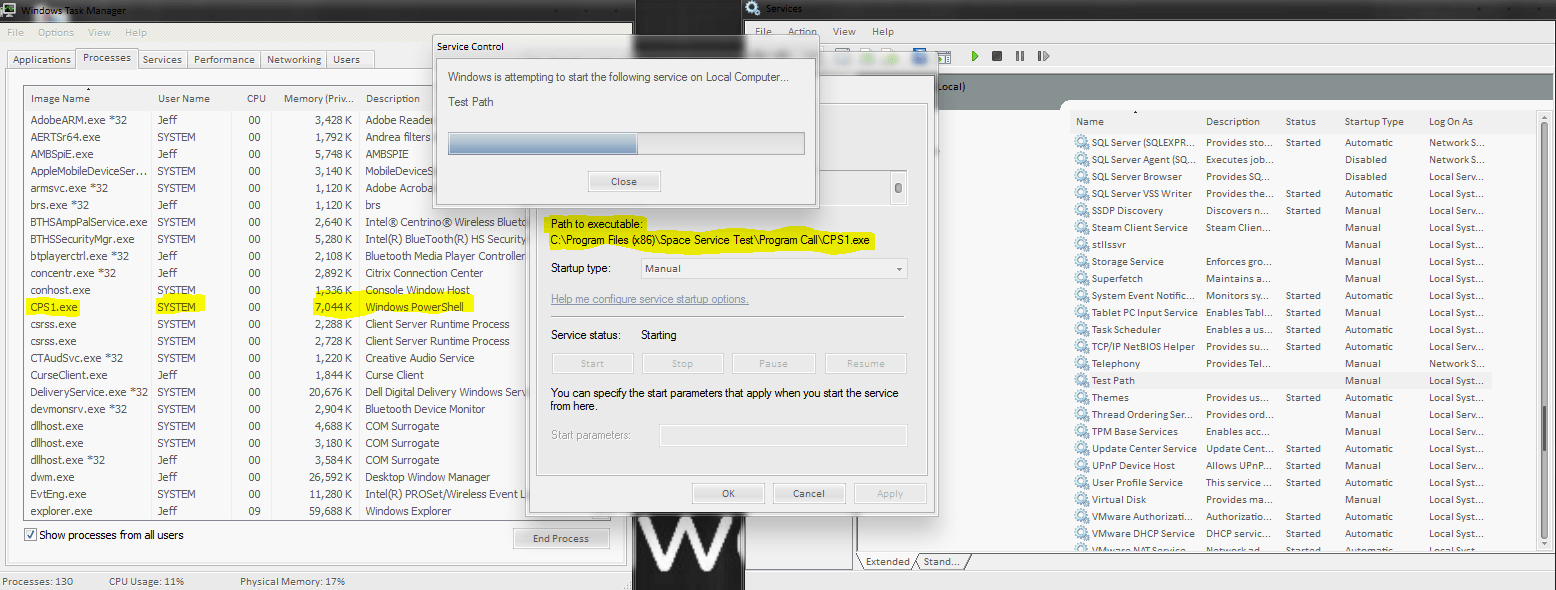
If you’re using a vulnerability scanner on your PC or network, you’ve probably come across the Microsoft Windows Unquoted Service Path Enumeration vulnerability. The truth is, this vulnerability has been

As many of us begin to upgrade to iOS 10 that was launched earlier today, we recommend that you check some of these settings to ensure your security and privacy

Everyone carries around their smartphones these days, and most don’t realize the amount of personal data that could be found on them if they ever made it into the wrong

If you’re a Mac user, you’ll want to make sure you’re using your computer as securely as possible. The common notion is that the MacOS is secure out-of-the-box, but the
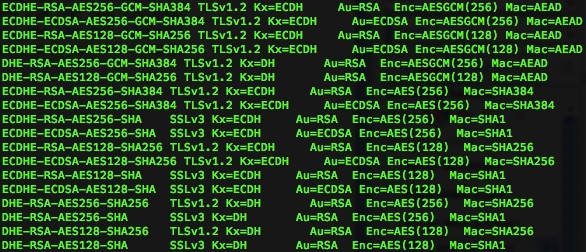
A few months ago, I wrote an article on how to configure IIS for SSL/TLS protocol cipher best practices. To test your configuration, you can use a handy tool called

While Windows Defender does a decent job at protecting your computer, Microsoft has a hidden feature built-in for the enterprise users. Luckily, a simple registry hack can increase your adware

