If you manage a Windows Certificate Authority for a Public Key Infrastructure (PKI), then you might run into an issue where some of your servers are using your auto-enroll group policy to request and renew a Remote Desktop certificate twice (or multiple) times per day. Looking in Event Viewer, you might see references to Event ID 64 and Event ID 65 in the Application logs referencing “certificateservicesclient-certenroll”. You’ll see that the certificates get installed successfully, but if you check your issuing Certificate Authority (CA), you’ll also see multiple certificates for that server each time it is renewed. It took some digging, but I finally came across Microsoft KB2531138, which suggests the Remote Desktop certificate template name and certificate template display name don’t match. Sure enough, they didn’t match because one had a space and the other didn’t.
How To Fix Server Renewing Remote Desktop Certificate Multiple Times Per Day
- Log into your Certification Authority and remove your Remote Desktop Template from the Certificate Templates
- Right-Click on Certificate Templates and select Manage
- Right-Click on your current Certificate Template and select Duplicate Template
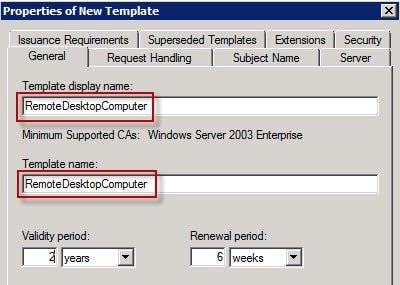
- Under the General Tab, make sure the new template uses the exact same Template Display Name and Template Name (including any spaces)
- Now go back to your Certificate Templates, right-click on the folder and select New > Certificate Template to Issue and select your new template
If you’re using Group Policy to set the Server Authentication Template, you’ll need to edit that Group Policy to reflect the new Certificate Template Name under Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Security > Server Authentication Template
If you notice a computer getting a new certificate multiple times per day (more than twice), then take a look in your Application Event Log and look for Event ID 1202 with a Source of SceCli. In my case, I saw errors about “Security policies were propagated with warning. 0x534 : No mapping between account names and security IDs was done.”
If you go to Start > Run and run rsop.msc, look for any errors in your Group Policy, particularly under Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment and Computer Configuration\Windows Settings\Security Settings\Local Policies\Restricted Groups. You probably have a policy that is referencing accounts that don’t exist on that server, which is causing it to attempt a Group Policy Update multiple times per day. You’ll need to edit your Group Policy and remove any of those accounts that don’t exist.