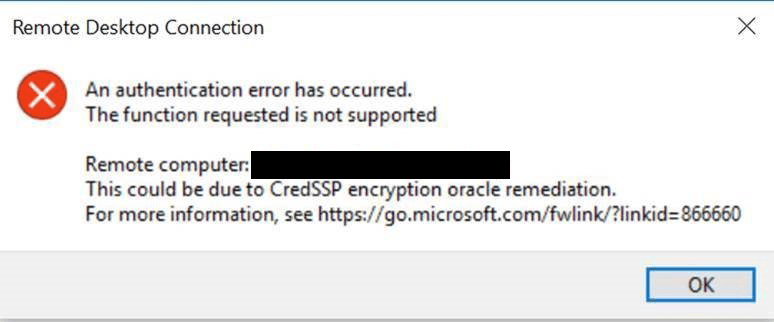
In March 2018, Microsoft released the CredSSP Updates for CVE-2018-0886, which is a vulnerability that could allow for remote code execution in unpatched versions of CredSSP. It would allow an attacker to relay user credentials to execute code on a target system. According to this Microsoft KB Article, they initially released an update in March. Then in April they released an update that would provide a more detailed error message while using the Remote Desktop Client (RDP). Then, finally, in the May 2018 Patch Tuesday, they just released an update that changed the default setting from Vulnerable to Mitigated which means that any client application that uses CredSSP will not be able to fall back to insecure versions. In other words, if you have a workstation that received the May update but a server that hasn’t received the CredSSP update, the workstation will receive the error message above when trying to RDP to that server.
Recommended Fix for Authentication Error Function Not Supported CredSSP Error
Obviously to reduce the risk of the vulnerability, the recommended solution is to patch all of the servers that are missing the update. Unfortunately, this update does require a reboot.
For more information, see the Microsoft article CredSSP updates for CVE-2018-0886.
Group Policy Temporary Workaround Fix for Authentication Error Function Not Supported CredSSP Error
If you cannot update your server right away, then the temporary workaround is to change a Group Policy. This is not recommended for a permanent solution since it means that the vulnerability could still exist on the servers.
Note: Ensure that you update the Group Policy Central Store (Or if not using a Central Store, use a device with the patch applied when editing Group Policy) with the latest CredSSP.admx and CredSSP.adml. These files will contain the latest copy of the edit configuration settings for these settings. If you do not have a patched server with access to Group Policy, then you won’t see the necessary settings because you’ll have an older version of CredSSP.admx and CredSSP.adml. You can try this copy of the ADMX and ADML files that I pulled from a patched Windows 2012 R2 server from my OneDrive.
- Copy these two files from a server with the updates or from the OneDrive link above:
C:\Windows\PolicyDefinitions\CredSsp.admx
C:\Windows\PolicyDefinitions\en-US\CredSsp.adml - On a Domain Controller, navigate to:
C:\Windows\SYSVOL\sysvol\\Policies\PolicyDefinitions - Rename the current CredSsp.admx to CredSsp.admx.old
- Copy the new CredSsp.admx to this folder
- Then navigate to:
C:\Windows\SYSVOL\sysvol\(or your local language)\Policies\PolicyDefinitions\en-US - Rename the current CredSsp.adml to CredSsp.adml.old
- Copy the new CredSsp.adml file to this folder
- Follow the Group Policy setting below
To set the Group Policy, create a new Group Policy and choose the best option that works for your case. Changing the setting to Vulnerable will allow you to connect to unpatched servers.
- Policy path: Computer Configuration -> Administrative Templates -> System -> Credentials Delegation
- Setting name: Encryption Oracle Remediation
Force Updated Clients – Client applications that use CredSSP will not be able to fall back to insecure versions, and services that use CredSSP will not accept unpatched clients. Note This setting should not be deployed until all remote hosts support the newest version.
Mitigated – Client applications that use CredSSP will not be able to fall back to insecure versions, but services that use CredSSP will accept unpatched clients.
Vulnerable – Client applications that use CredSSP will expose the remote servers to attacks by supporting fallback to insecure versions, and services that use CredSSP will accept unpatched clients.
Registry Temporary Workaround Fix for Authentication Error Function Not Supported CredSSP Error
To make the changes on a single computer (or on a computer not connected to a domain), you can create this registry key (This is not recommended for a permanent solution since it means that the vulnerability could still exist on the servers):
Windows Registry Editor Version 5.00[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters]
"AllowEncryptionOracle"=dword:00000002
The registry key can be set to:
- 0 – Force Updated Clients – Client applications that use CredSSP will not be able to fall back to insecure versions, and services that use CredSSP will not accept unpatched clients. Note This setting should not be deployed until all remote hosts support the newest version.
- 1 – Mitigated – Client applications that use CredSSP will not be able to fall back to insecure versions, but services that use CredSSP will accept unpatched clients.
- 2 – Vulnerable – Client applications that use CredSSP will expose the remote servers to attacks by supporting fallback to insecure versions, and services that use CredSSP will accept unpatched clients.
Final Reminder
Remember that the Group Policy and registry edits are NOT RECOMMENDED for a permanent solution. As soon as the servers in your environment are patched, you’ll want to change the Group Policy and registry key back to defaults to ensure protection against this vulnerability.