Tag: security
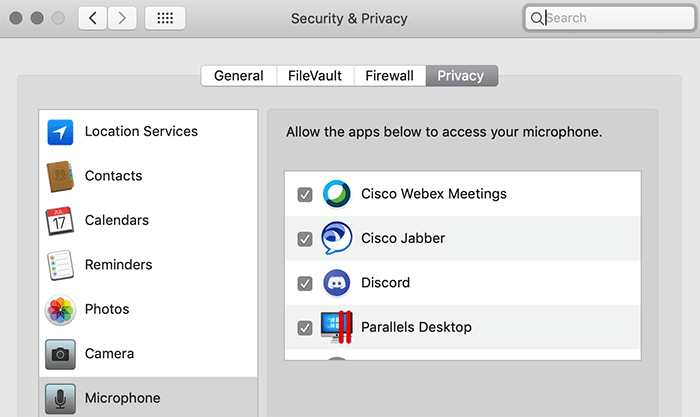
If you’re having an issue getting your camera or microphone working in certain apps after upgrading your Mac to macOS Mojave, it could be related to some of the …
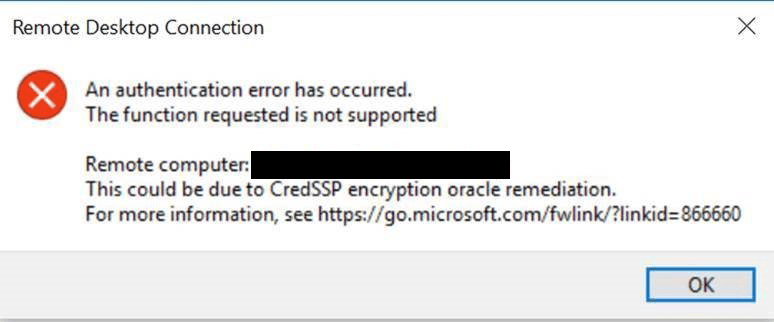
In March 2018, Microsoft released the CredSSP Updates for CVE-2018-0886, which is a vulnerability that could allow for remote code execution in unpatched versions of CredSSP. It would allow …
If you followed my previous guides for LEMP Install NGINX PHP7 MySQL on Ubuntu 16.04 Server then you probably installed NGINX from the Ubuntu repo. Unfortunately, the version in …
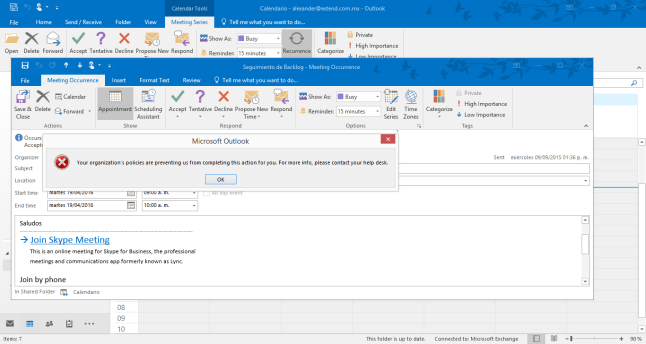
I recently ran into an issue where Outlook 2016 on Windows 10 was giving me one of these errors whenever I would try to click on a link: “This …
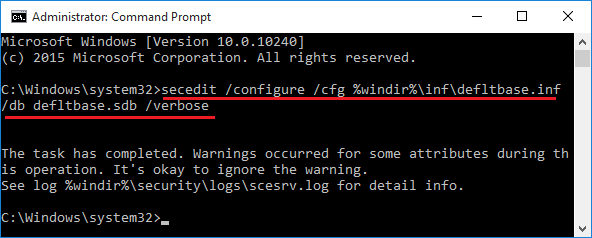
If you recently tried applying a Group Policy or Local Policy in Windows and are having odd side effects, or notice the policy doesn’t seem to be working as …
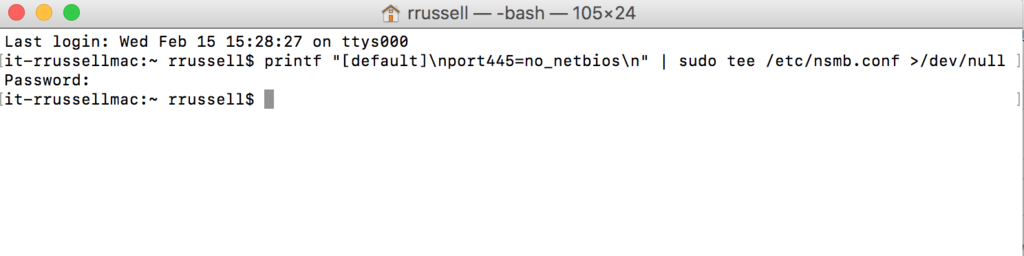
Even though my network has NetBIOS disabled in my Windows environment, including on the Windows DHCP server, the Mac OS X computers on the network still want to send …
MongoDB is “a document database that provides high performance, high availability, and easy scalability”. In this chapter of our InfoSec System Hardening series, we’ll walk you through some of …
The next segment in our InfoSec System Hardening series is how to harden an NGINX Web Server. NGINX is an alternative to the popular Apache Web Server on Linux. …
As with any server, whether it be a web server, file server, database server, etc, hardening is an important step in information security and protecting the data on your …
A zero-day local privilege escalation vulnerability has been found in the Linux kernel that has existed since 2005, being called DirtyCow. This bug affects a large number of popular …