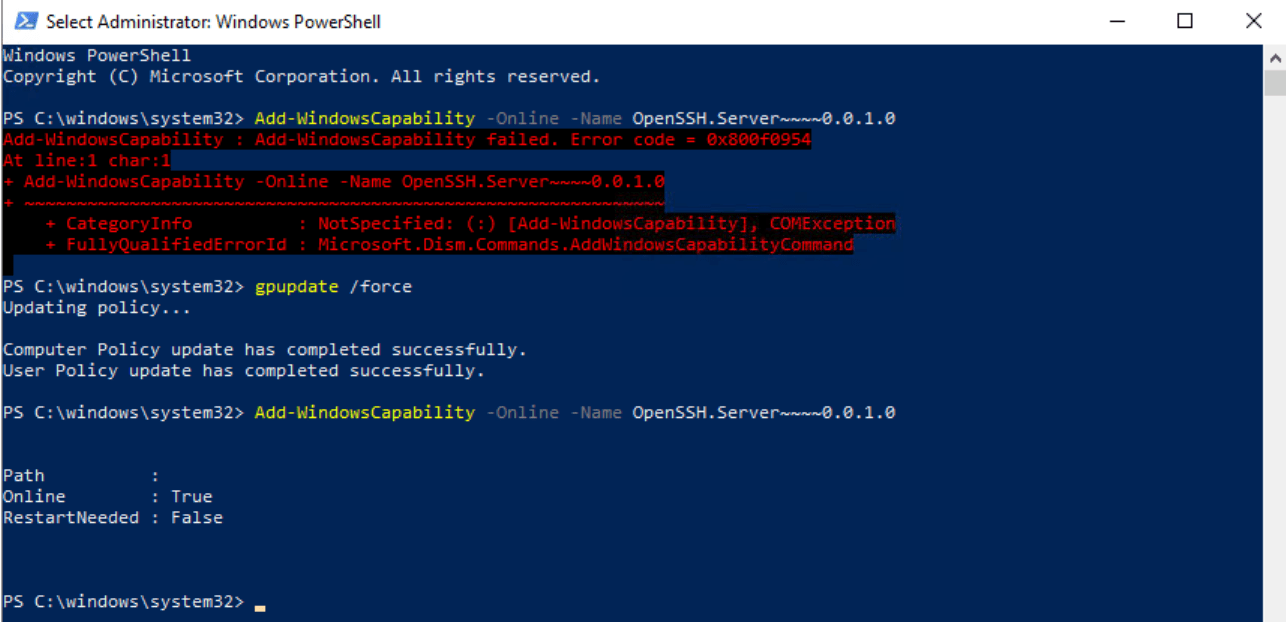
If you have tried to install a Windows Compatibility feature in Windows 10, Windows 11, Windows Server 2019, or Windows Server 2022, you might have come across: Add-WindowsCapability failed. Error
Author: Rob Russell

Depending on the version of Windows, you might run into an issue where Powershell is using an older TLS version which could cause errors. Recently, there’s been an industry-wide push,

The Azure CLI is a useful tool for managing various aspects of Azure. If your company uses a proxy service, it might replace the root and intermediate certificates for HTTPS

Unapproved Outlook Add-Ins can pose a security risk to organizations. Some add-ins can ask for more permissions to a user’s mailbox than an organization prefers and depending on the add-in’s

After upgrading to Ubuntu 22.04 LTS, you might run into errors trying to start your Docker containers similar to “Error response from daemon: OCI runtime create failed: container with id
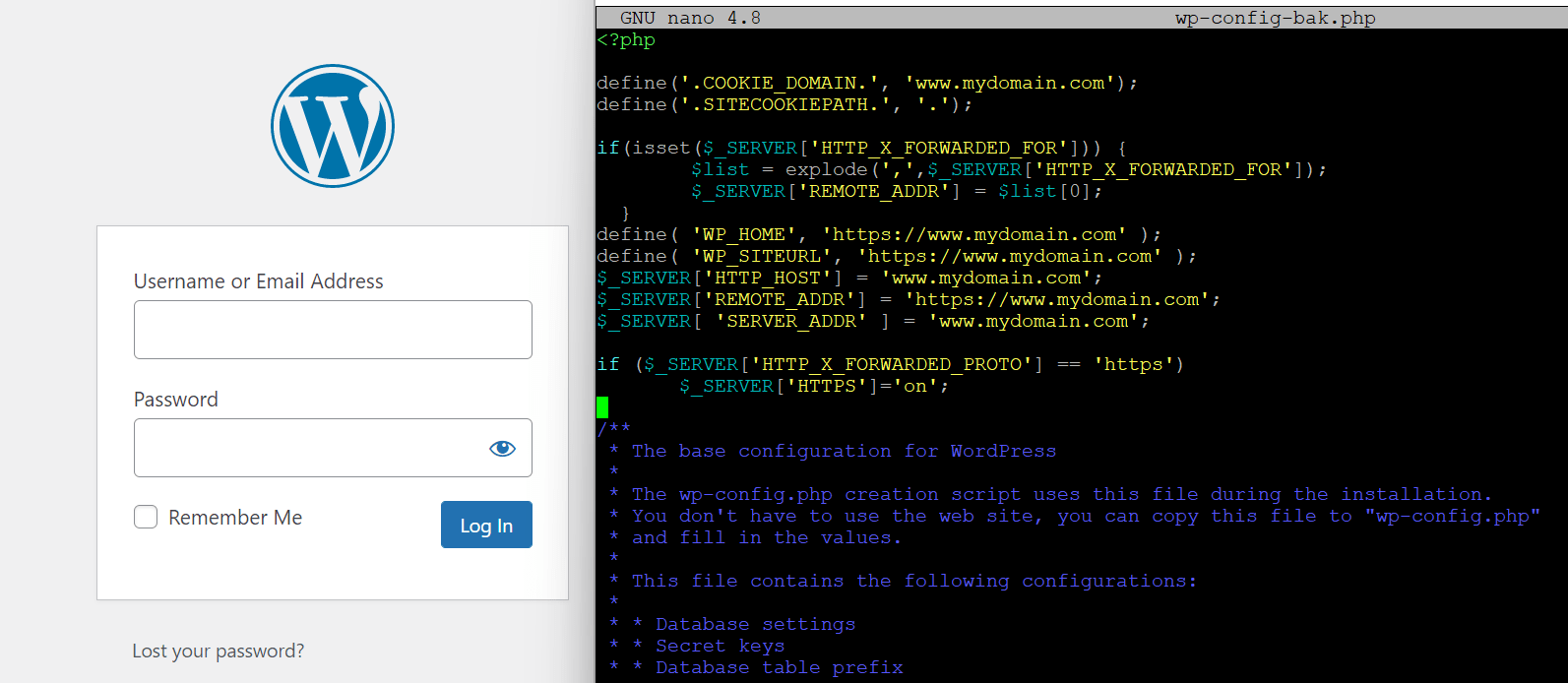
Wordpress installation are usually straightforward. Unfortunately, if you’re using a reverse proxy like Caddy or NGINX in front of your WordPress webserver, you’ll likely run into issues with too many

If you ever run into a situation where you have a stuck session state in the connections table in a Check Point firewall, you can refer to SK103876 (You must

If you’re noticing VMMem high CPU usage in Windows 10 or Windows 11, it is related to the Windows Subsystem for Linux (WSL and WSL2). More recently, it seems to

Log4j is a Java library for logging error messages in applications and is a critical security vulnerability with a severity score of 10 out of 10. The high score is
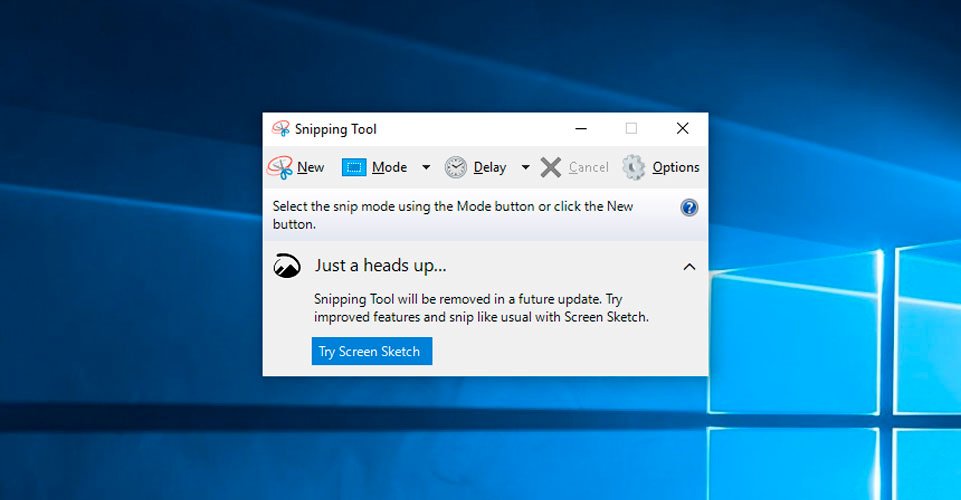
Updated July 4, 2024: Added information to map the old Snipping Tool to a hotkey (keyboard shortcut). If you recently upgraded to Windows 11, you will notice that old Snipping