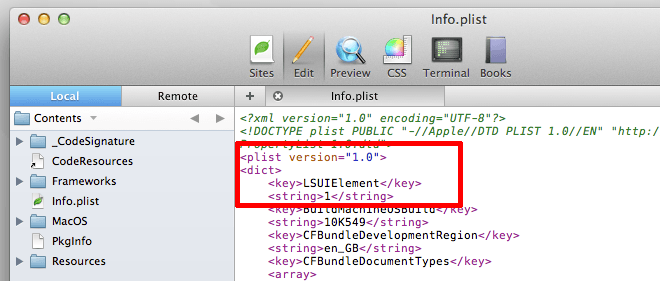
Until Teamviewer devices to build an option into the app that hides the dock icon, the only way to remove it is through some hacks. Since it is in the
Tag: sysadmin

I recently ran into the error message “Failed to open the runspace pool. The Server manager WinRM plug-in might be corrupted or missing.” shortly after deploying a new Windows 2012

I recently had an issue on a MySQL Database Server where running apt-get upgrade to upgrade the MySQL package on the server would result in an error about the table

MongoDB is “a document database that provides high performance, high availability, and easy scalability”. In this chapter of our InfoSec System Hardening series, we’ll walk you through some of the

The next segment in our InfoSec System Hardening series is how to harden an NGINX Web Server. NGINX is an alternative to the popular Apache Web Server on Linux. In

As with any server, whether it be a web server, file server, database server, etc, hardening is an important step in information security and protecting the data on your systems.
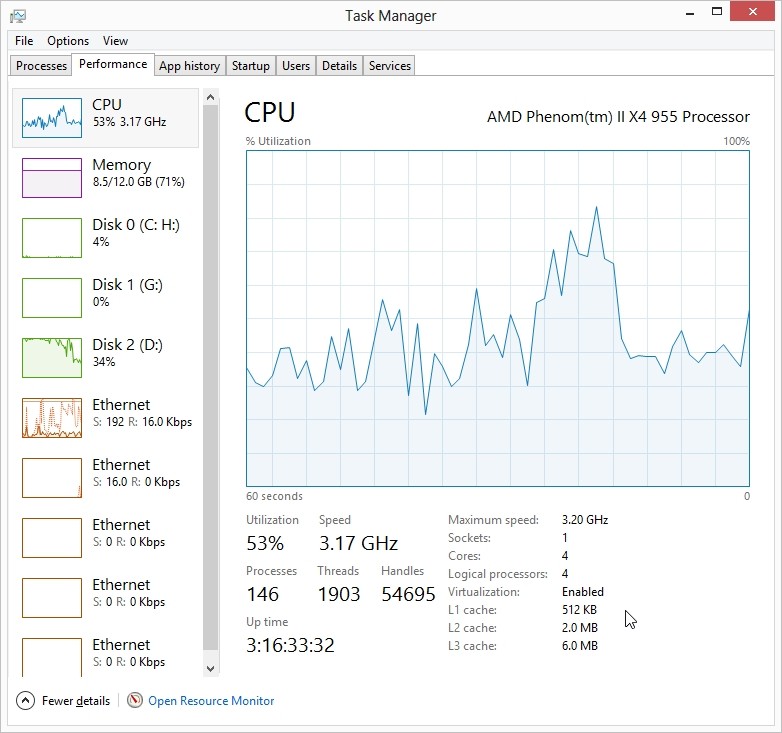
Windows Server 2012 and Windows 10 came with a lot of changes to the task manager and in some cases the default views have been simplified further than power users
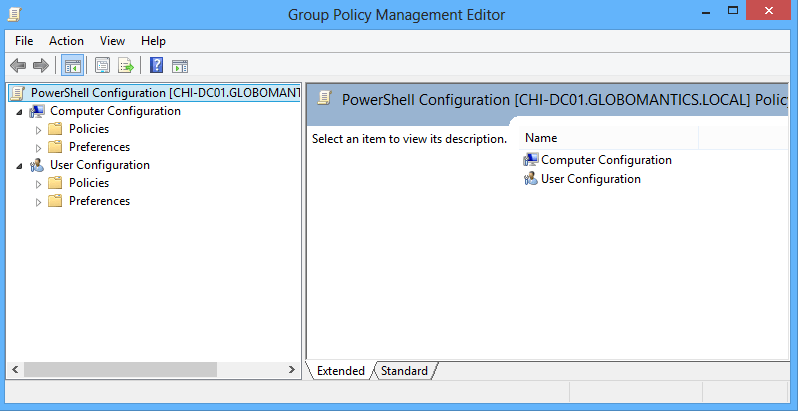
As a Systems Administrator, you’ve probably worked with Group Policy before, especially if you’re in a Microsoft Windows environment. Group Policy allows you to push out settings to multiple computers

“How do I find a Cisco serial number remotely through the command line?” This is one of those frequently asked questions that I see over and over. So, here’s the

There are a few options you have if you want to enable audit logging on Microsoft SQL Server. You can write the logs to a .sqlaudit file, but you cannot