As an addition to my previous NGINX articles, today we’ll discuss how to adjust the number of child processes for PHP-FPM to fix the common error of “server reached pm.max_children”
Tag: linux
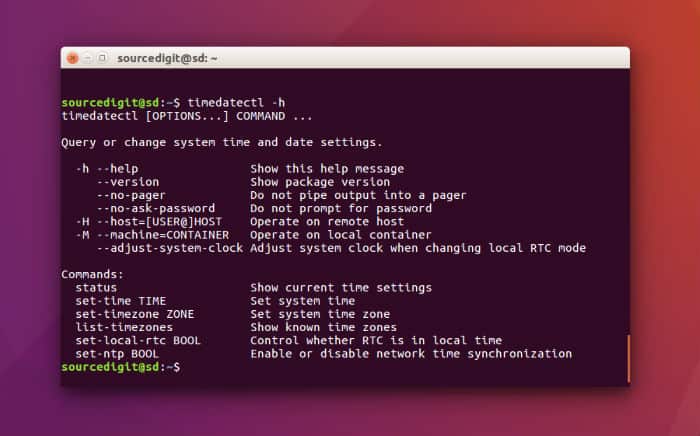
I recently came across an issue where an Ubuntu 14.04 LTS server wasn’t syncing the time so the jitter and drifting of the time wasn’t correcting itself. This caused issues

A DNS server resolves website URLs into their IP addresses, which is how the internet functions. Without DNS, we would be typing in IP addresses into our browsers instead of

A zero-day local privilege escalation vulnerability has been found in the Linux kernel that has existed since 2005, being called DirtyCow. This bug affects a large number of popular Linux

If you’re running a WordPress site on a Linux server running NGINX, then you might be interested in setting up a free SSL (HTTPS) certificate using Let’s Encrypt. The internet

Tor is free software and an open network. Tor protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents

If you’re using a version of Debian Linux like Ubuntu, Kali, Mint, etc, then this tutorial will help you in getting Google Chrome running on your system. The commands will
Since I’m fairly new at Linux and I have successfully got sendmail working on my server for my domain, I thought I would write this walkthrough to help others configure

