Microsoft has released an online troubleshooting tool to help you resolve your Windows Update errors if you’re running Windows 10, Windows 8.1, or Windows 7. If you’re running Windows 8,
Category: System Administration
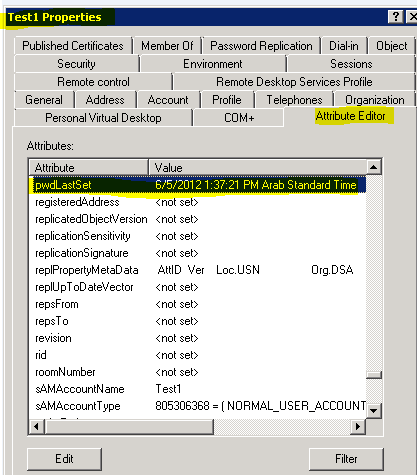
Active Directory account passwords are usually set to expire (for example: every 90 days) in most organizations. Configuring an AD account with PasswordNeverExpires is not recommended due to security. There
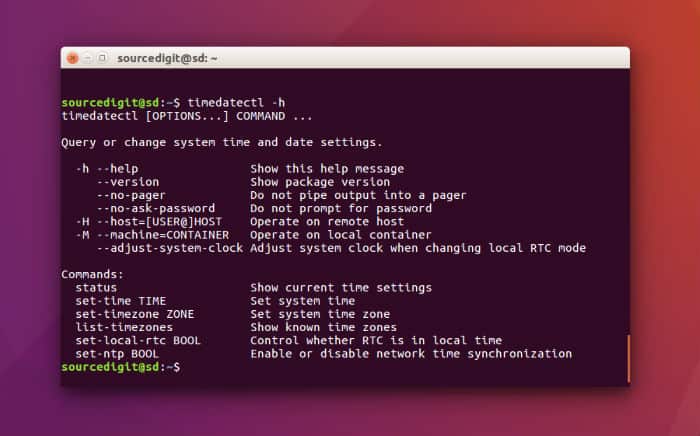
I recently came across an issue where an Ubuntu 14.04 LTS server wasn’t syncing the time so the jitter and drifting of the time wasn’t correcting itself. This caused issues

A DNS server resolves website URLs into their IP addresses, which is how the internet functions. Without DNS, we would be typing in IP addresses into our browsers instead of
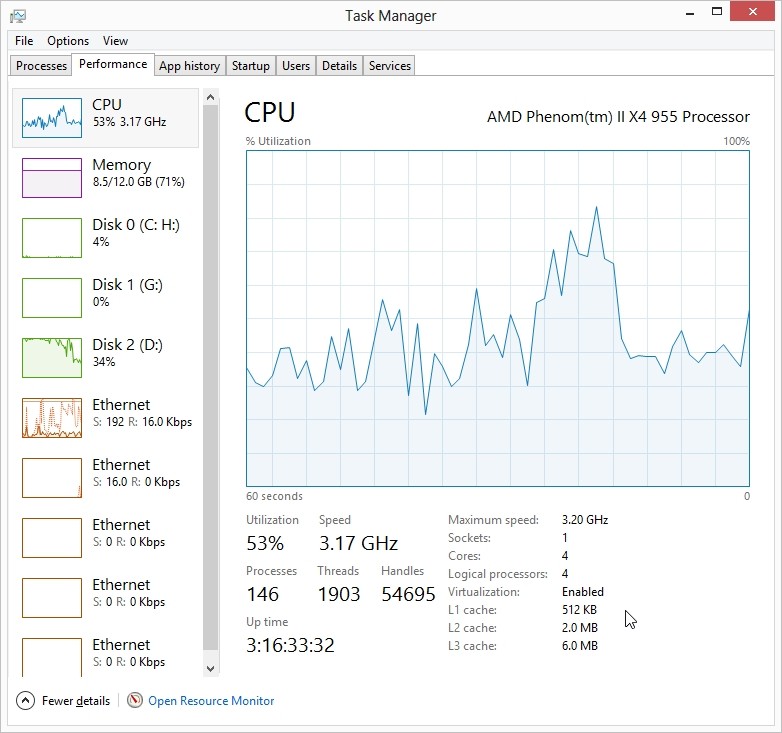
Windows Server 2012 and Windows 10 came with a lot of changes to the task manager and in some cases the default views have been simplified further than power users

A zero-day local privilege escalation vulnerability has been found in the Linux kernel that has existed since 2005, being called DirtyCow. This bug affects a large number of popular Linux
As a Systems Administrator, you’ve probably worked with Group Policy before, especially if you’re in a Microsoft Windows environment. Group Policy allows you to push out settings to multiple computers

If you’re running a WordPress site on a Linux server running NGINX, then you might be interested in setting up a free SSL (HTTPS) certificate using Let’s Encrypt. The internet
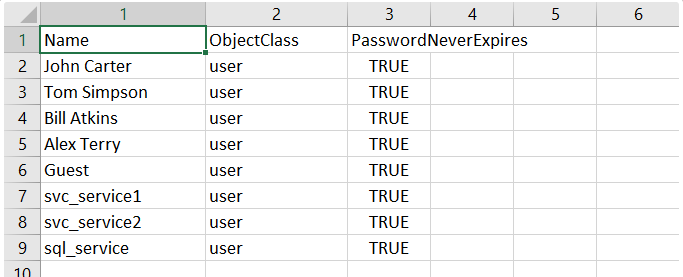
As a Systems Administrator, it is always a good security measure to audit your Active Directory accounts on a regular basis. Tools like Netwrix can help automate this process by
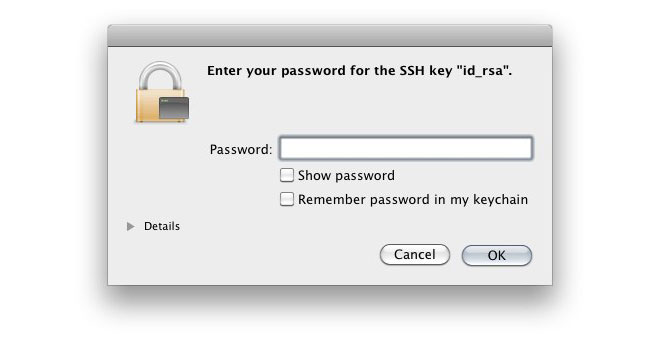
If you’re a systems administrator and you’ve recently upgraded to Apple’s macOS Sierra, you may have noticed that macOS now stores your SSH key passphrase by default, without even giving

